One of the most common ways viruses can get into your network is by email. With a little bit of imagination, an attacker can send out an email message to your organization that will entice your users to infect their computers by opening attached files.
A recent would-be attacker was very creative:
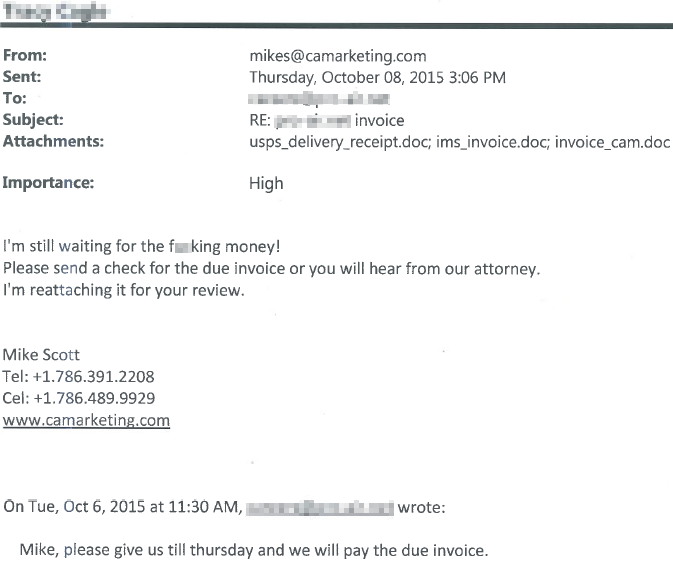
Notice that the email creates a sense of urgency.
With the choice of wording, formatting, and attached filenames, a user may see this as a legitimate email and think the business owes the sender money. There is even a thread at the bottom showing a fake reply accepting this debt and promising to pay it two days prior.
If the user were to investigate this email’s authenticity, they may open one of the three attached documents. Then the user could simply decide the email is a scam and delete it. But it will be too late. The virus has already infected their computer. Furthermore they may not even be aware of it because the virus is dormant waiting for activation by the attacker.
Our email security protection blocked this message before it had a chance.
Pro-Computer Services, Inc. provides solutions to secure your network from threats like these. We use special firewalls and services that scan your email for viruses, spam, and malware before it even arrives in your inbox.
Still, no business can be 100% safe using security products and services alone.
Some of these creative emails will slip through the cracks. All of the anti-Spam and firewalls products are “dumb-devices”. They cannot know the actual context by which your users conduct daily business. There will be false positives indicating some good messages are bad and some bad messages as good. Devices do not know you or your contacts and their personalities, vocabulary, or how they communicate.
Pro-Computer Services creates smart-users out of your employees by offering training to our Pain-Free IT customers. Your users will then recognize these threats as malicious and not be fooled by such creative messages.
There are a few questions to ask yourself when receiving questionable email.
- Do I actually know the sender?
- Am I expecting an email from this sender about this subject?
- Does the email have attachments with filenames that do not make sense?
- Does the email have hyperlinks to a legitimate website?
- Is the email professionally written?
Next time you receive a questionable email stop and ask yourself these questions or call us at Pro-Computer Services (256-353-4476) and ask us about how we can create smart-users out of your employees.
